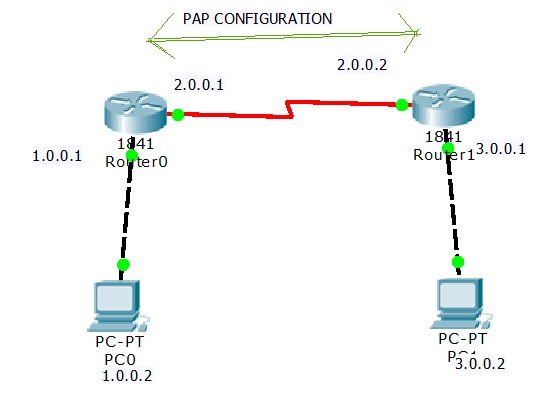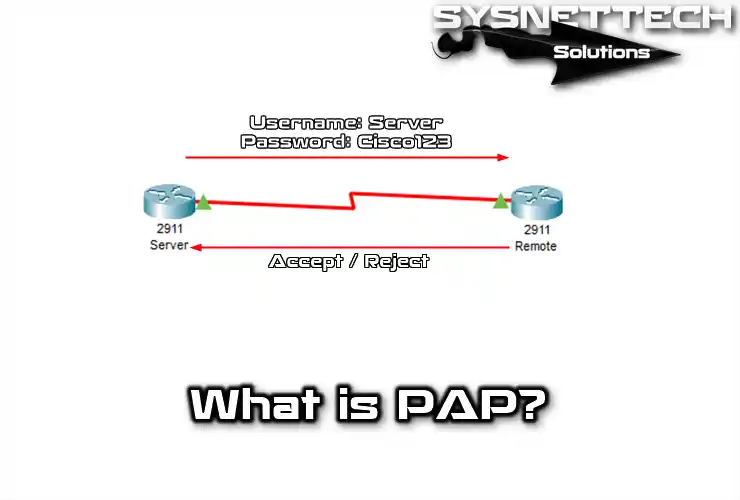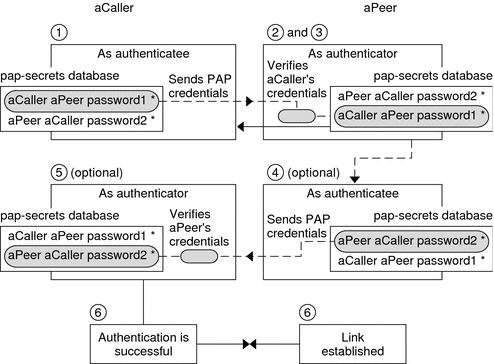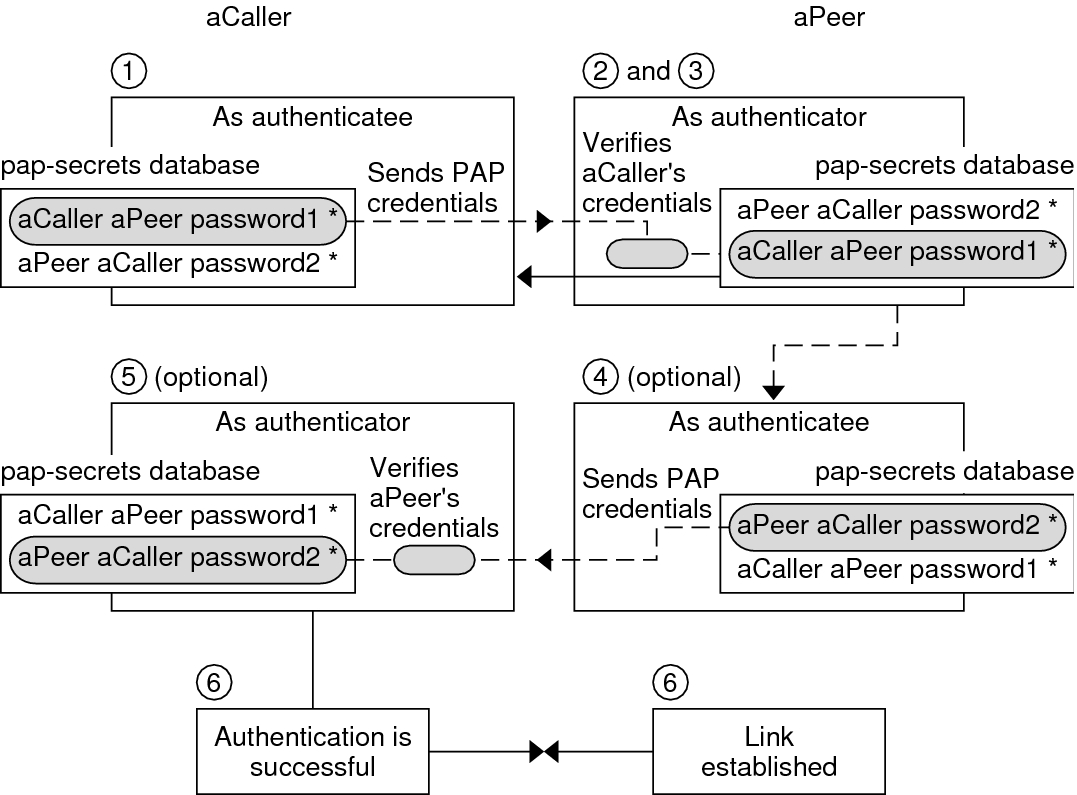
Password Authentication Protocol (PAP) - Managing Serial Networks Using UUCP and PPP in Oracle® Solaris 11.2
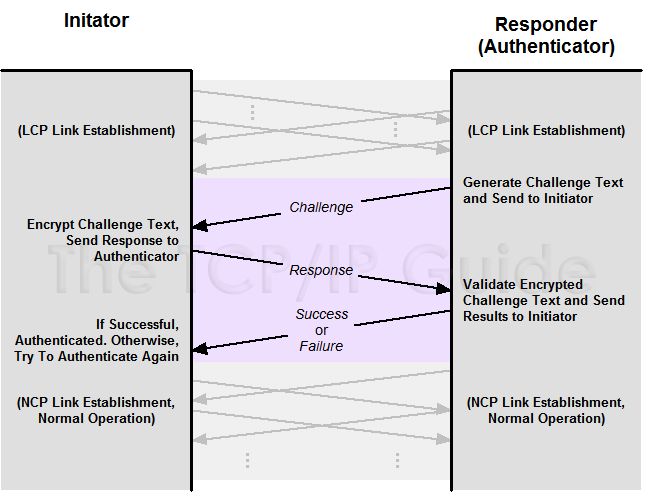
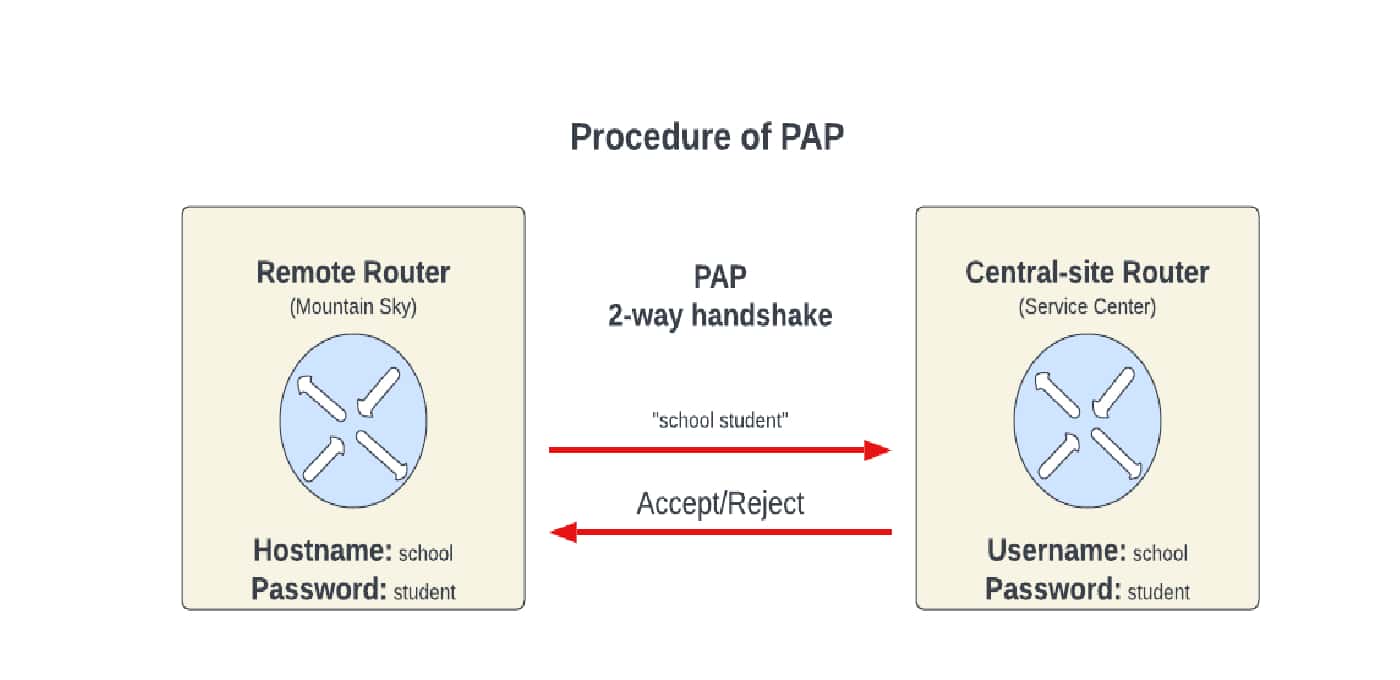
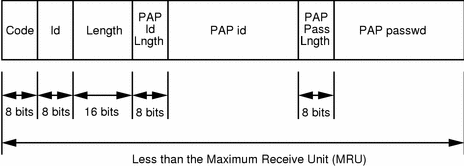
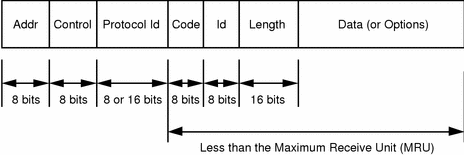
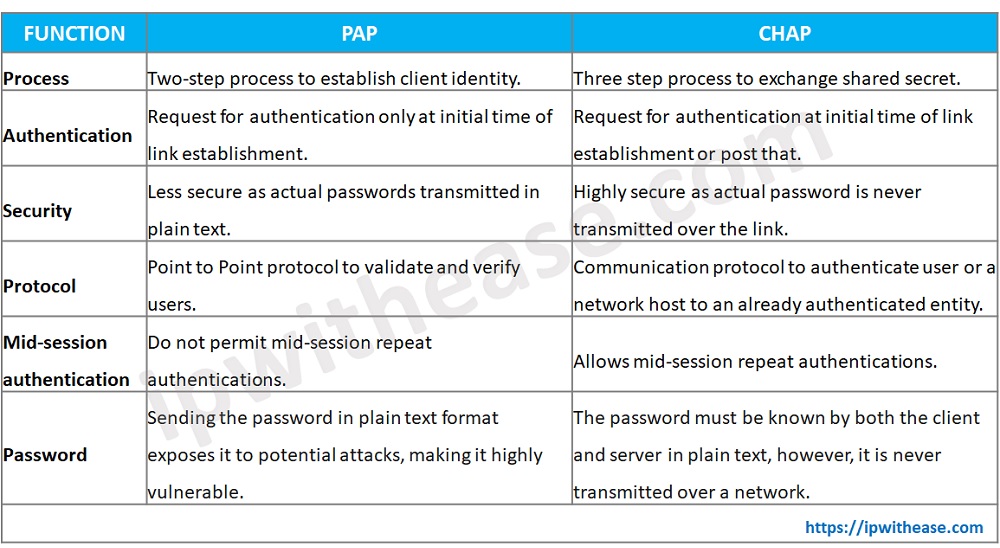
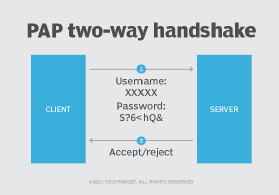
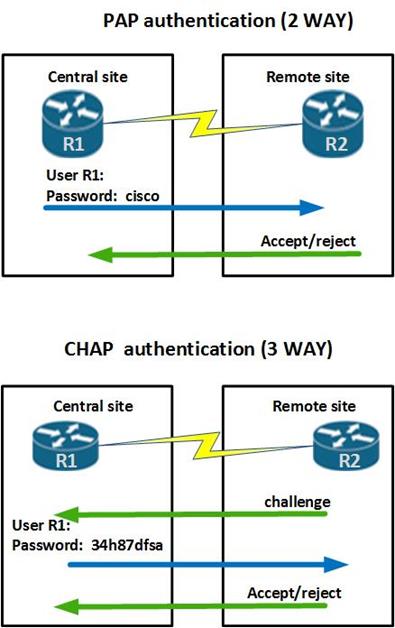
The TCP/IP Guide - PPP Authentication Protocols: Password Authentication Protocol (PAP) and Challenge Handshake Authentication Protocol (CHAP)

Pap Password Authentication Protocol Acronym Stock Illustration - Download Image Now - Acronym, Business, Computer - iStock
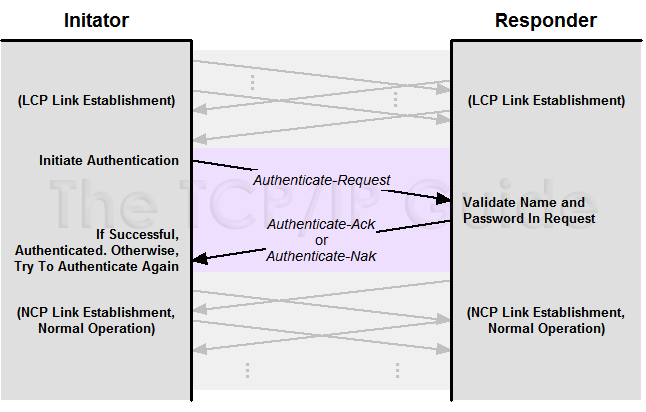
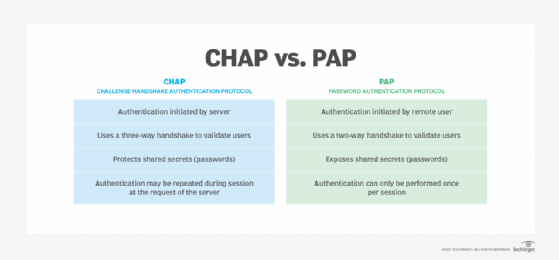
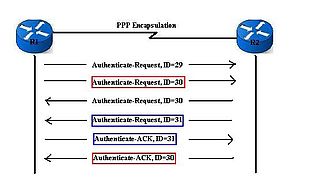
The TCP/IP Guide - PPP Authentication Protocols: Password Authentication Protocol (PAP) and Challenge Handshake Authentication Protocol (CHAP)